Security and Privacy
To do so, an application presents a Seam Connect Webview, which handles walking a device owner through selecting their manufacturers and authorizing them.
Seam then manages a device session with the manufacturer on behalf of the third-party application.
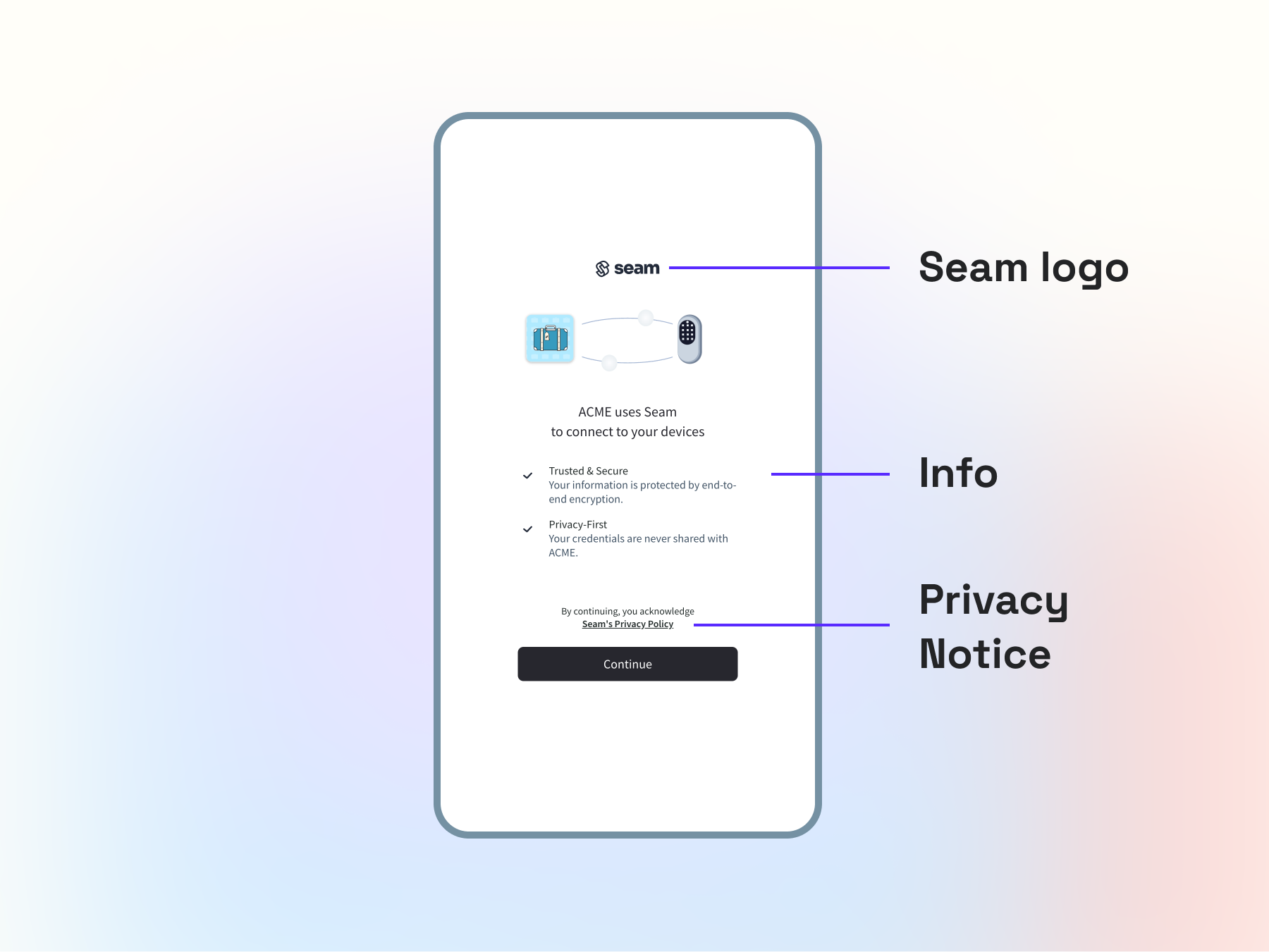
When a Connect Webview is first presented to the user, the initial screen explains what Seam is, its relationship to the application, and briefly explains how data is secured. No matter the third-party application, Seam's name, logo, and privacy policy are present on this screen to be transparent to the user. We do not allow modifications to this screen or any other screens in the Connect Webview flow.

In the event that Seam must collect device account credentials (see next sections), we continue to display the Seam logo prominently to ensure that there is no confusion as to where the user is and with whom they are sharing their credentials. In the absence of Seam’s logo, the sole presence of a manufacturer's logo may lead users to think they are on a domain/page owned by the manufacturer.
Obtaining Device Sessions
How this authorization is done varies from manufacturer to manufacturer. Seam’s preferred approach is to have OAuth integrations with each manufacturer. In the absence of this option, Seam is required to collect and retain device login credentials. We are actively working with manufacturers to reduce the prevalence of this approach by providing them with OAuth implementation help.
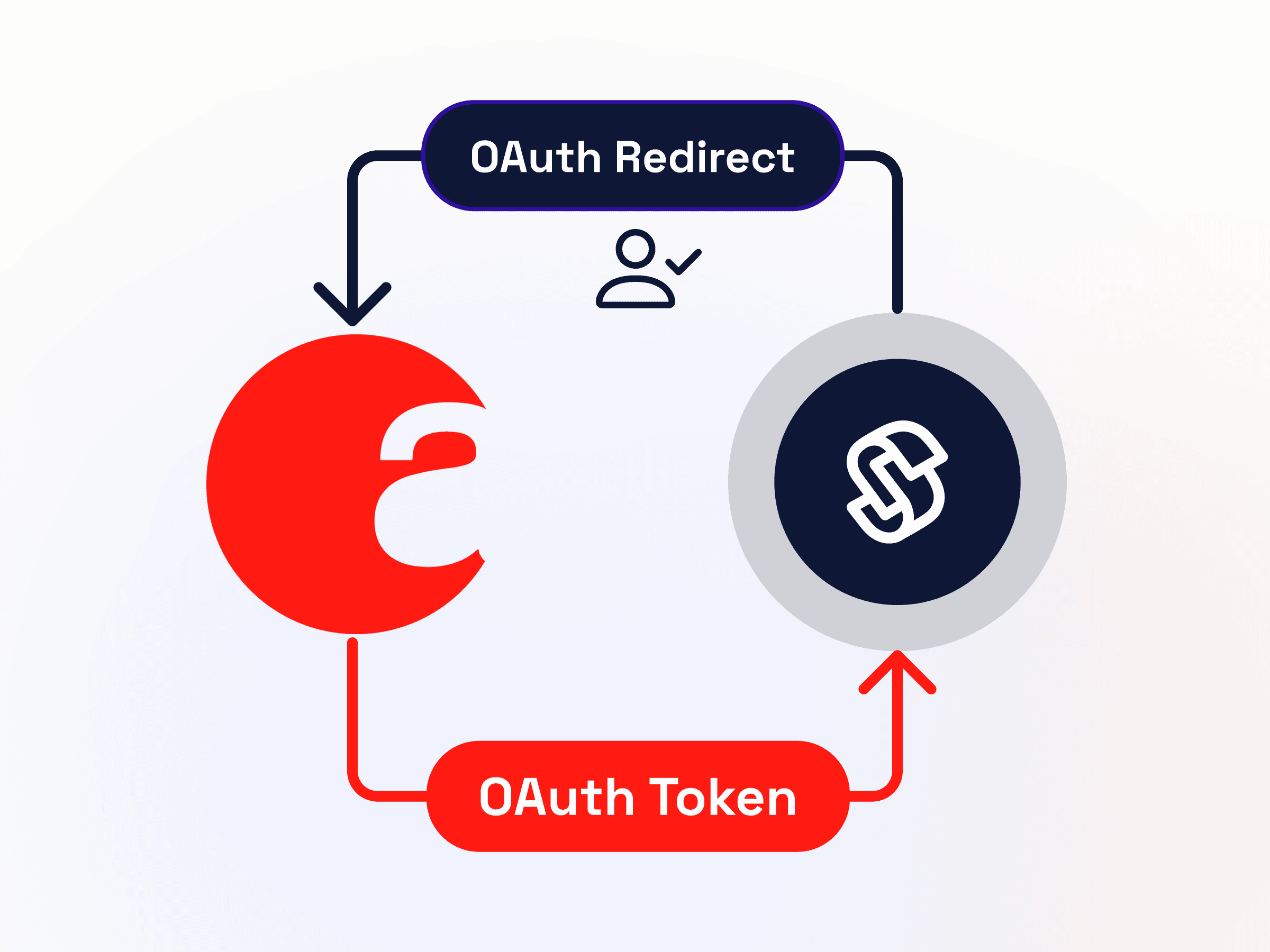
This is our preferred way to connect to a third-party account. It ensures that we never have to collect or retain device credentials. We are working together with manufacturers to increase OAuth support for their devices.
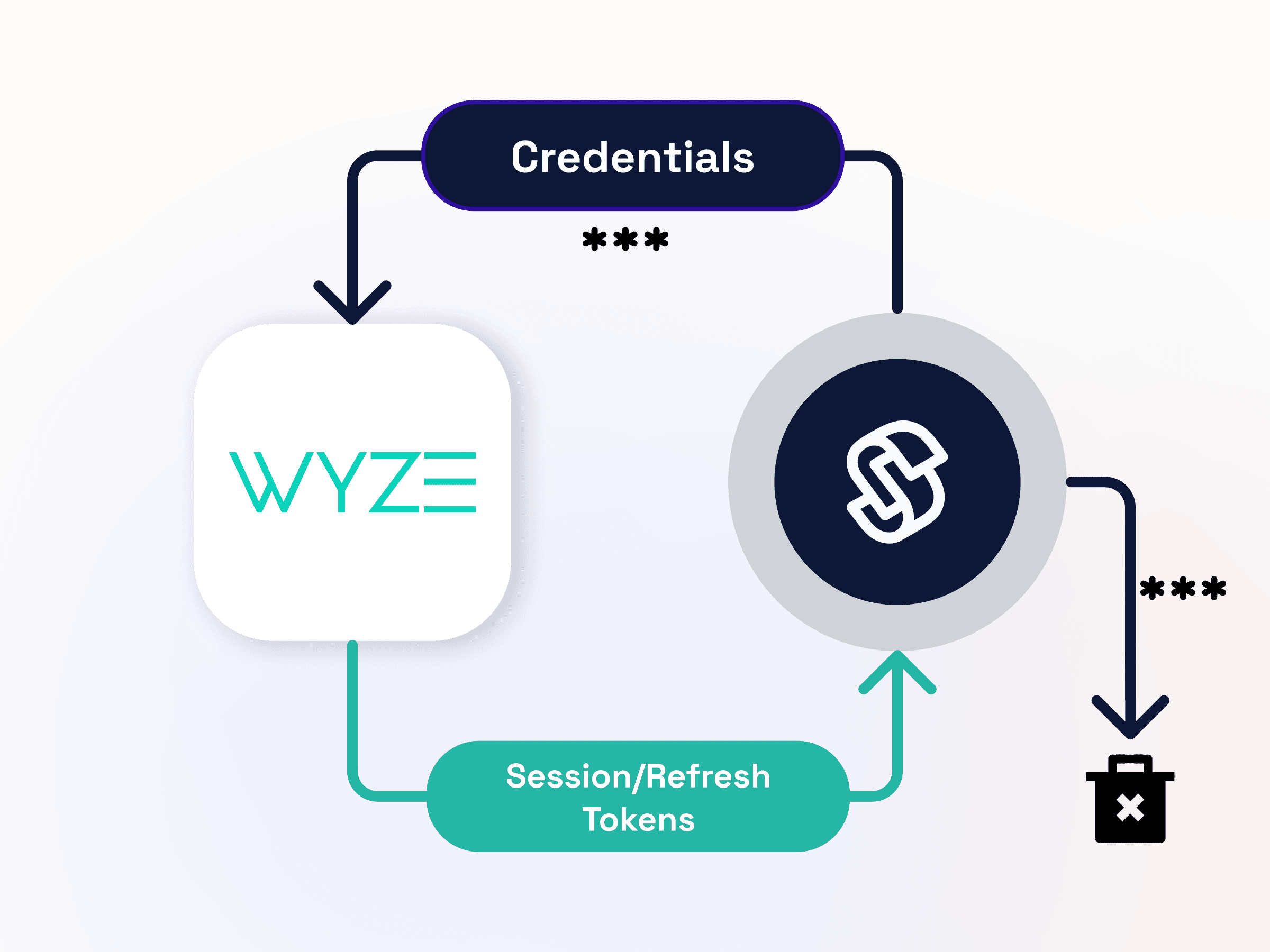
When a manufacturer does not support OAuth, Seam will collect credentials from the device owner to establish a session. When a refresh token is returned by the manufacturer, we store this token and delete the device credentials.
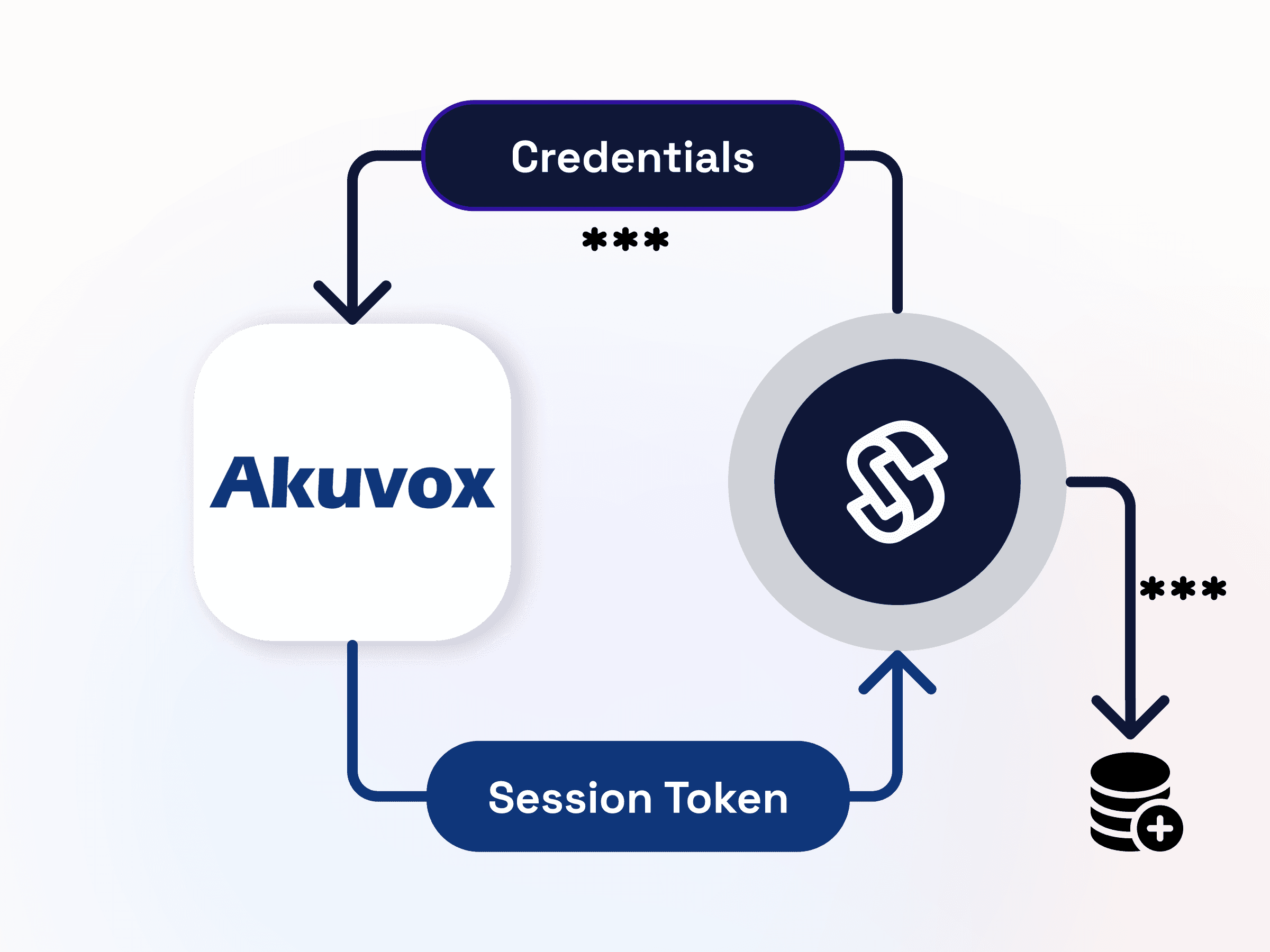
In the event that a manufacturer does not support OAuth and does not return a refresh token, we are required to collect and retain the full device credentials in order to manage the device on behalf of its owner on an ongoing basis. These are stored in a secure database that is encrypted at rest, with limited access to our team.
In partnership with device manufacturers, we are also exploring ways to add additional transparency for device owners to see which applications have access to their devices.
Only the workspace that requested access to a device account and its associated devices can control those devices. Another workspace that has not explicitly been authorized by the device owner will not be able to control the device or its associated account. Note that there is one exception to this rule: a workspace owner can grant access to devices in their workspace by creating a Personal Access Token (PAT).
If device owners decide that they no longer want to share access to their device, they have a few options for disconnecting their device account. First, if the device manufacturer offers OAuth (see prior section), their device app may have a menu where they can revoke access. Second, Seam implements an account disconnection endpoint. This lets a third-party app offer a way for the user to disconnect their accounts directly from within this application. In the event that the third-party app does not have such a feature, we honor disconnection requests at support@getseam.com after verifying device account ownership. We are working together with developers to increase the availability of device management apps that offer a way to disconnect accounts. We are also exploring offering a device-owner facing portal that shows them which third-party apps have access to their devices.

When device owners grant access to their devices to third-party apps through Seam, the full set of device functions supported by Seam will become available in those third party apps. In instances where OAuth is available and the manufacturer has implemented a list of permissions that can be explicitly revoked, Seam is not able to circumvent those permissions and will only provide access to the set of selected permissions. When the manufacturer does not offer OAuth or a set of granular permissions, we are actively exploring letting device owners disable certain device capabilities based on their preferences as well as schedules. This is an intricate feature to build, and we do not have a firm timeline for now.

We develop tools to manage our customers, their workspaces, and the associated device accounts. By default, a Seam employee has NO access to a customers’ workspace. In order to obtain this access, a Seam employee must request access on a per workspace basis. This access request is reviewed and granted by a much smaller subset of authorized individuals at Seam. We are constantly re-evaluating how to reduce access and permissions scope without overly burdening our team. We plan on continuing to add layers of security and access permissions to our internal tools.

Seam stores a set of device properties and metadata, such as device battery level, device serial number, and in some instances, location as entered by the users in their device management applications. These properties are available to the third-party applications requesting authorization to the device and systems. These are generally used to help troubleshoot devices (e.g. low battery alert), as well as assist users in managing their devices
When a device emits an event (e.g. door unlocking), Seam will receive it. Most of the time, there is limited metadata around the event itself. Since we avoid collecting personal information, we’re generally not able to determine who performed the event. However, a third-party application authorized against the device will also receive the event and might have personal information beyond what Seam has in order to make that determination. For example, if we report which pin code was used to unlock a door, the third-party application might be able to match that code to a specific individual
We treat API keys as passwords. We generate them, and we return the key to the client. We store the short-token and a hash. We are not able to see your full keys after generating them.
All Seam API keys are prefixed with the token “seam_”. We also participate in credential scanning programs on popular code hosting platforms to alert you if you accidentally commit your Seam API keys.
Seam webhooks are signed using an HMAC with SHA-256. If you wish to verify those signatures on your end, contact our team.
We require 2-factor authentication for our team on nearly all accounts. We generally discourage the use of SMS-based 2FA and issue security keys to all of our team members.
Removal of a Warrant Canary implies that Seam is subject to one or more legal proceedings preventing it from making that statement.
Seam has never received a secret government request to hand over user information.
Seam has never installed law enforcement software or equipment in our stack or network.
Seam has never turned over our SSL keys or our customers' SSL keys to anyone.
Seam has never provided any law enforcement organization a feed of our customers' data.
Seam has never terminated a customer because of political pressure.
Seam has never weakened, compromised, or subverted any encryption at the request of law enforcement or a third party.
Seam has never modified customer data at the request of law enforcement or a third party.